The other day I came across this scam page, and I was surprised to see that it shows up in Bing search results:
hxxp://explorersecuritysuite .com/info.php?af=213&url=http://www.facebook.com/login.php
This alert appears in any browser, even if you go directly to the site. The scam page pretends that you're getting an official warning from Microsoft.
The page claims:
This website has been reported as unsafe
We strongly recommend to discontinue the use of this website.
[link] Activate my Web protection software
This website has been reported to Microsoft for containing threats that might steal personal or financial information from your computer
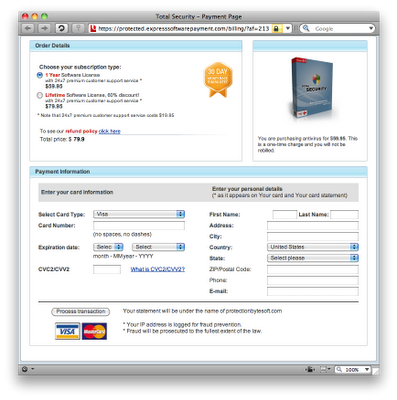
...and if you further click on "Click Here!" you'll be taken to this page:
A non-savvy Web user could easily be tricked by the initial warning into following the links, perhaps even thinking that Microsoft wanted them to buy this "Total Security" product (or perhaps not thinking, due to fear of identity theft and a frantic desire to protect oneself). After all, what could make someone feel safer online than "total security"? But surely a more seasoned individual, say for example an advanced Microsoft employee, wouldn't be tricked by such a scheme. Or would they?
I followed Microsoft's directions for submitting malicious sites, and dutifully reported the deceptive page to Microsoft's Bing support team. A friendly lady from Bing Technical Support replied and said that "I understand that you are reporting a scam site listed in Bing results. I know the importance of this issue. I will now be escalating your email to our product specialists for further investigation. They will directly take action on your request and will be contacting you with an update soon." That sounded very promising. Imagine my surprise when I got this response later:
Hello Joshua,
We have already reported the www.explorersecuritysuite .com. If you check the query on BING, you should be able to see the warning on the vertical result.
I have provided a link for the query:
http://www.bing.com/search?q=explorersecuritysuite.com
Thank you for reporting this matter.
Best Regards,
[name redacted]
Microsoft Global Escalations
Of course, the search query brings up the malicious page at the very top of the results, as seen here:
However, there's no warning from Microsoft anywhere on the search results page. The closest thing is Bing's quotation of the scam page. I replied to Microsoft's Global Escalations representative, explaining that "The site itself is malicious, and it pretends to have been reported to Microsoft. Try the direct malicious link in any other browser and you'll get the same warning when you visit the page. The warning comes directly from the site, not from Bing or Microsoft. This is clearly not an official Microsoft alert." I provided a direct link to the malicious page (non-sanitized, in case this individual might have been confused by hxxp or a space in the domain name). I sent this reply well over 24 hours ago. I still haven't gotten a response, and the scam page is still indexed on Bing.
So, how about that? Even someone who works for Microsoft's Global Escalations department can get fooled by a malicious scam site.
UPDATE: Two days after I sent my last reply to Microsoft Global Escalations, a different representative responded:
Hello Josh,
My name is [redacted] with Microsoft Global Escalations.
I have re-investigated the said site ([unsanitized URL redacted]) and would confirm with you that the site is indeed misleading.
We will be taking action to remove this as soon as possible.
Thank you for reporting this and again brining [sic] this to our attention.
Best Regards,
[name redacted]
Micsrosoft Global Escalations [sic]
Yet another two days after getting this reply, the site was finally removed from Bing. So from the time I first reported the site to Microsoft until it actually got delisted from Bing's search results was roughly 5.5 days.
Fun storytelling aside, here's the technical stuff, for anyone who might be interested.
http://wepawet.iseclab.org/view.php?hash=493989f2a5387f5176781a3f11e969e8&t=1253948333&type=js (Wepawet analysis showing affiliated domains)
http://www.mywot.com/en/scorecard/explorersecuritysuite.com (Web of Trust report)
A nearly identical domain, windowssecurityinfo .com, also comes up in Bing search results, although the site is not loading at the moment:
http://www.bing.com/search?q=windowssecurityinfo.com (example Bing search that brings up this actual domain as a result, just like with explorersecuritysuite)
http://cc.bingj.com/cache.aspx?d=76745708601589&w=4c13551f,ac670a51 (Bing cache, not linked because it tries to load images and CSS directly from the domain; use caution)
http://www.malwareurl.com/listing.php?domain=windowssecurityinfo.com
http://www.mywot.com/en/scorecard/windowssecurityinfo.com
Related fake warning sites that are currently inactive:
browsersecurityinfo .com
http://malwaredatabase.net/blog/index.php/2009/07/08/website-selling-multiple-rogue-programs-as-legitimate-pt-2/
http://wepawet.iseclab.org/domain.php?hash=c9e5f4ba1f2a19e94c0294ab39f499ea&type=js (Wepawet analysis showing affiliated domains)
http://www.malwareurl.com/listing.php?domain=browsersecurityinfo.com
http://www.mywot.com/en/scorecard/browsersecurityinfo.com
suspiciousdomainblock .com/pre1/?af=14s1
http://www.cybertechhelp.com/forums/showpost.php?p=1116477&postcount=1
http://wepawet.iseclab.org/view.php?hash=1ef044d5571341b35240cd8fa4f843e0t=1249738635&type=js (Wepawet analysis showing affiliated domains)
http://www.malwareurl.com/listing.php?domain=suspiciousdomainblock.com
http://www.mywot.com/en/scorecard/suspiciousdomainblock.com
Reports for affiliated domains:
http://www.mywot.com/en/scorecard/winnetworkstatus.com (redirects from explorersecuritysuite to expresssoftwarepayment)
http://www.mywot.com/en/scorecard/expresssoftwarepayment.com (including protected.expresssoftwarepayment .com)
http://www.mywot.com/en/scorecard/protectionbytesoft.com ("Eco Antivirus"/"Total Security" fake AV site, mentioned on payment page)
http://www.mywot.com/en/scorecard/cnnnewspoint.com (redirected from suspiciousdomainblock to authorized-payments)
http://www.mywot.com/en/scorecard/authorized-payments.com (including protected.authorized-payments .com)
http://www.mywot.com/en/scorecard/cyberstrongstore.com ("Eco Antivirus"/"Total Security" fake AV site, mentioned on payment page)
http://www.mywot.com/en/scorecard/ieprotectionlist.com (linked from browsersecurityinfo)
http://www.mywot.com/en/scorecard/bennysaintscathedral.com (redirected from ieprotectionlist to buysecuritysoftwareonline)
http://www.mywot.com/en/scorecard/buysecuritysoftwareonline.com (including secure.buysecuritysoftwareonline .com)
Fake warning sites from a different fake/rogue antivirus campaign, all of which are currently active:
hxxp://safewebway2009 .com/warning/
http://www.mywot.com/en/scorecard/safewebway2009.com
hxxp://trusted-web-way .com/warning/
http://www.mywot.com/en/scorecard/trusted-web-way.com
hxxp://protect-my-web .com/warning/
http://www.mywot.com/en/scorecard/protect-my-web.com
hxxp://rightsafeway .com/warning/
http://www.mywot.com/en/scorecard/rightsafeway.com
hxxp://web-safe-and-clean .com/warning/
http://www.mywot.com/en/scorecard/web-safe-and-clean.com
All of these sites redirect to hxxp://yesantivirusplus .com/buy.php?id=
http://www.mywot.com/en/scorecard/yesantivirusplus.com
Payment site for Antivirus Plus: hxxps://my-secure-payment .com/cgi-bin/nph-pr/pandora/softcore/buy_soft.php?productid=avplus4&advert=
http://www.mywot.com/en/scorecard/my-secure-payment.com
More fake warning pages:
hxxp://www.malwareurl.com/search.php?s=Fake+Warning&urls=on&redirs=on (site defunct, and URL was not saved on archive.org)