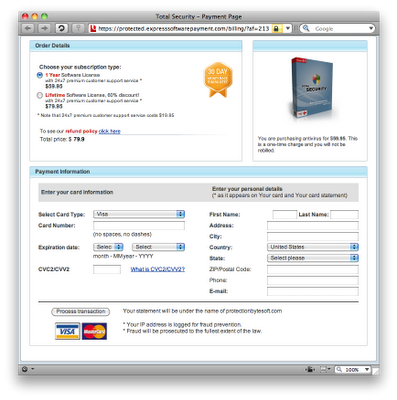
Tonight my wife searched Google using the seemingly harmless query "season 6 sytycd winner" to find out the final results from this season of So You Think You Can Dance, a popular TV show in the U.S., and she was surprised to find that the first link she clicked (the third result in the list) redirected her browser to a fake virus scan very similar to the one described here.
The search result page was hosted on modaentertainment .com, and it redirected to a fake virus scan hosted on antyvirusaccessory .net. The page tries to trick the user into downloading malware which has the following characteristics (information courtesy of VirusTotal):
File name: install.exeSee also the following Panda Xandora and ThreatExpert behavioral analysis reports:
File size: 1190464 bytes
MD5...: 0a4f8f846759d81f750cd68a80d33790
SHA1..: 7d9da6a60fb7b92ce9b7514cafd7c2f3e8ff2776
SHA256: 7dcfa255c93d1d678dfd2a059b26d3a29bad53907e86538126cba260c1a37caf
8/41 detection rate as of 2009.12.17 03:39:01 (UTC)
24/41 detection rate as of 2009.12.19 19:59:55 (UTC)
26/41 detection rate as of 2009.12.21 06:01:43 (UTC)
Variously identified as: a variant of Win32/Kryptik.BJS, FraudTool.Win32.RogueSecurity (v), Heuristic.LooksLike.Trojan.FraudPack.H, Mal/FakeAV-AD, RogueAntiSpyware.SecurityToolFraud, Suspicious file, Suspicious:W32/Malware!Gemini, W32/FakeAlert.DX3.gen!Eldorado, Dropper.Win32.Mnless.fph, FakeAlert-KC.d, FakeAlert.NZ, Heur.Suspicious, Heuristic.LooksLike.Worm.Koobface.H, Rogue:W32/FakeAlert.gen!S, Trojan:Win32/Winwebsec, Trojan.FakeAv.ZQ, Trojan.FraudPack.aeft, Trojan.Packed.18037, Trojan.Win32.FakeAV, Trojan.Win32.FakeAV!IK, Trojan.Win32.FraudPack.aeft, Trojan.Win32.Generic!SB.0, W32/FraudPack.AEFT!tr, Win32:FakeAlert-FJ, Worm/Koobface.aeh, Trojan.FakeAV-261, Trojan.FraudPack.SAP, etc.
http://xandora.security.net.my/?p=1631 [site is no longer accessible]
http://www.threatexpert.com/report.aspx?md5=0a4f8f846759d81f750cd68a80d33790 [archive]
For additional information on the sites spreading this malware, see my Web of Trust reports for these domains:
https://www.mywot.com/en/scorecard/antyvirusaccessory.net
https://www.mywot.com/en/scorecard/modaentertainment.com
According to Google Safe Browsing, the modaentertainment site has ties to securityonlineforum .net, a known malware site which shares the same IP address (193.104.153 .2) as the antyvirusaccessory site and several other malicious domains:
https://www.mywot.com/en/scorecard/securityonlineforum.net
http://www.malwareurl.com/ns_listing.php?ip=193.104.153.2 [archive]
UPDATE, 19 Dec 2009 @ 19:40 PST: I've included new detection names for the initial variant above. Also, the download URL now hosts a different variant of this malware (information courtesy of VirusTotal: sample 1, sample 2):
File name: install.exeSee also the ThreatExpert behavioral analysis report.
File size: 1192512 bytes
MD5...: 998b769df2ac21db9dd3471e89c2828a or ef18948dfa176dbf0e6666f297cf7ee8
SHA1..: 648dc270bc501ee24c43ae155291c602e7ff5c8b or c3d383c7e0912de6dce1f2299bc1325131741b80
SHA256: 7d390d8229c4dc4da844e05d0c3f8c98b308c5d43f0dc2930bc718b2854e591e or 512668f04ba6ec8060fa1755ca38bc2e9ca2384fa6601232032bb90f965fe24e
Sample 1: 13/41 detection rate as of 2009.12.19 20:01:49 (UTC)
Sample 2: 15/41 detection rate as of 2009.12.20 03:14:18 (UTC)
Sample 2: 19/41 detection rate as of 2009.12.21 06:01:53 (UTC)
Variously identified as: a variant of Win32/Kryptik.BMB, FakeAlert-KW, FraudTool.Win32.RogueSecurity (v), Heuristic.LooksLike.Worm.Koobface.H, High Risk Cloaked Malware, Mal/FakeAV-AD, Malware-Cryptor.Win32.General.8, RogueAntiSpyware.SecurityToolFraud, Suspicious file, Trojan.Win32.FakeAV, Trojan.Win32.FraudPack.aewt, TrojWare.Win32.FraudTool.TS.~FGA, W32/FakeAlert.DX3.gen!Eldorado, Generic16.DCM, TR/FraudPack.aewt, Trojan.FraudPack.SAO, Trojan.Packed.18524, etc.
UPDATE, 20 Dec 2009 @ 22:10 PST: Added 2 more detection names for the first variant and 4 more names for the second variant.
UPDATE, 29 Dec 2009 @ 08:10 PST: Once again, the download URL is hosting a different variant of this malware (information courtesy of VirusTotal):
File name: install.exeSee also the Panda Autovin (formerly known as Xandora) and ThreatExpert behavioral analysis reports:
File size: 1167872 bytes
MD5...: a3e56b9f93ccd164f2618b1cb5afc32d
SHA1..: 6bffc64505903cad0b203eb6e41321ac625e1a3a
SHA256: ff0e91e944c606aafd918b8209dedb26c12b801deea5ed0c2407f3a0d5ddd787
8/41 detection rate as of 2009.12.28 19:35:31 (UTC)
20/41 detection rate as of 2009.12.29 15:44:10 (UTC)
Variously identified as: a variant of Win32/Kryptik.BFY, ApplicUnsaf.Win32.FraudTool.ST.~CRS, Artemis!A3E56B9F93CC, FakeAlert-KW, FakeAlert.OF, Heuristic.LooksLike.Worm.Koobface.H, In-Trojan/Fakealert.1167872, Mal/FakeAV-BT, Mal/Generic-A, Medium Risk Malware, Packed.Win32.Krap.ai, RogueAntiSpyware.SecurityToolFraud, Trj/CI.A, Trojan.Fraudpack.Gen!Pac.4, Trojan.Packed.19519, Trojan.Win32.FakeAV, Trojan.Win32.FakeAV.arh, W32/FakeAlert.OF!tr, Win32.WormKoobface.B, Worm.Koobface, Worm/Koobface.bpy, etc.
http://autovin.pandasecurity.my/?p=2017 [site is no longer accessible]
http://www.threatexpert.com/report.aspx?md5=a3e56b9f93ccd164f2618b1cb5afc32d [site is no longer accessible]
For more from the JoshMeister on Security, please subscribe to the RSS feed or follow me on Twitter.